This Acceptable Use Policy (“AUP”) describes activities that are not allowed in connection with your use of the Email Deployment Platform Services. The AUP is incorporated by reference in your Agreement with Email Deployment Platform.
The Internet is still evolving, and the ways in which the Internet may be abused are also still evolving. Therefore, we may from time to time amend this AUP to further detail or describe reasonable restrictions on your use of our Services by publishing a revised version of the AUP at https://www.UnikAdv.com/aup, or in the event of a material adverse change to the AUP, by providing you thirty (30) days written notice.
If you breach this AUP we may limit, suspend, or terminate your account in accordance with our Terms of Use. We may intercept or block any content or traffic belonging to you or to users where services are being used unlawfully or not in accordance with this AUP.
1) Requirements. Customer will follow these guidelines when sending emails and SMS using the Service:
1a – All email sending metrics to remain within Email Deployment Platform’s thresholds:
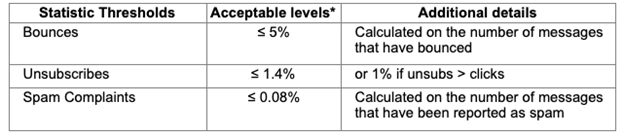
Calculated on the number of messages that have been reported as spam
*Unik Adv’s Email Deployment Platform reserves the right to update the parameters of the acceptable sending threshold without prior notice.
1b – Acquiring or sending to a mailing list without opt-in records (as indicated by date and time stamps) is prohibited. Use of contact lists that are bought or scraped from third-parties is prohibited by law in most countries, and is absolutely prohibited on Unik Adv’s Email Deployment Platform servers.
1c – Emails and SMS (unless transactional) can only be sent where permission has been expressly obtained in nature, and can only be sent to recipients who have granted clear, explicit and provable consent to receive communication. This consent should be granted through a confirmed single or double opt-in system that clearly expresses the topic of the subscription on an online or offline form via an unmarked by default checkbox.
1d – Proof of consent must be provided in the event of an escalated abuse complaint. We take escalated abuse complaints received from recipients very seriously. At any given moment, you must be able to provide information regarding all email addresses and/or telephone numbers to which you’ve sent emails and/or SMS through the platform (including the basis of the obtained consent, when and how the email address or telephone number was collected, and any other pertain proof of legal permission to contact the recipients).
1e – An unsubscribe link must be included in every marketing email campaign. All marketing campaigns must include a clear and concise link for recipients to easily opt-out of receiving future communication. The link must be easy for anyone to recognize, read, and understand. You must honor unsubscribe requests without undue delay. For marketing SMS, you must provide all the end-users the right to opt out of receiving any further SMS sent by you. Note that transactional and confirmation emails and transactional SMS do not require an unsubscribe link.
1f – Sender name and status must be clearly communicated in every email message. “From”, “To” and “Reply-To” fields must accurately and clearly identify the sender’s domain name and email address. When sending from a different domain name on behalf of a partner or related third-party organization, the email body must clearly communicate that the message is sent via a third-party domain. Any third-party domains must also be validated by the sender.
1g – Readily publish on your website and comply with a privacy policy that meets legal requirements and include a link to that policy in the body of each email.
2) Prohibited Behavior
You may not use our platform or Services to engage in, foster, or promote illegal, abusive, or irresponsible behavior, including (but not limited to):
- 2a – Any activity or conduct that is likely to be in breach of any applicable laws, codes or regulations, including data privacy laws and laws relating to unsolicited commercial electronic messages;
- 2b – Any activity intended to withhold or cloak identity or contact information, including the omission, deletion, forgery or misreporting of any transmission or identification information, such as return mailing and IP addresses;
- 2c – Interference with the Services. Interfering with or otherwise negatively impacting any aspect of the Services or any third-party networks that are linked to the Services.
3) Prohibited Content
You may not publish, transmit or store on or via the Services any content or links to any content that Email Deployment Platform reasonably believes is illegal, harmful, unwanted, or otherwise poses a threat to the public. Moreover and unless the sender gives us sufficient and specific guarantees at our sole discretion, we do not work in principle with senders who promote the following activities or sends content, whether permitted by law or not, that includes the following, but is not limited to:
- Any payday loans, debt collection agencies, affiliate marketing, or anything that can be considered abusive or dishonest;
- Any gambling activity in violation of any required licenses, codes of practice, or necessary technical standards required under the laws or regulations of any jurisdiction in which your site is hosted or accessed;
- Constitutes, depicts, fosters, promotes or relates in any manner to child pornography, bestiality, non-consensual sex acts, or otherwise unlawfully exploits persons under 18 years of age;
- Publish, transmit or store any content or links to any content that is excessively violent, incites violence, threatens violence, contains harassing content or hate speech, creates a risk to a person’s safety or health, or public safety or health, compromises national security or interferes with an investigation by law enforcement;
- Is unfair or deceptive under the consumer protection laws of any jurisdiction, including chain letters and pyramid schemes;
- Is defamatory or violates a person’s privacy; or
- Is otherwise malicious, fraudulent, morally repugnant.
4) Excessive Use of Shared System Resources
You may not use any shared system provided by Email Deployment Platform in a way that unnecessarily interferes with the normal operation of the shared system, or that consumes a disproportionate share of the resources of the system. For example, we may require you to repair coding abnormalities in your application if it unnecessarily conflicts with other Email Deployment Platform customers’ use of the Services. You agree that we may quarantine or delete any data stored on a shared system if the data is infected with a virus, or is otherwise corrupted, and has the potential to infect or corrupt the system or other customers’ data that is stored on the same system.
5) Email Validation Requirements
Without limiting the application of any other provisions of this AUP, with respect to any of the Services’ email validation features or functionality, you may not:
- 5a – Use the Services to verify the email address(es) of any person who has not affirmatively consented (i.e., opted-in) to, or who has expressly opted-out from receiving email communications from you;
- 5b – Use the Services to validate email addresses that were purchased, rented or similarly obtained from a third party (i.e., third party email lists); or,
- 5c – Use the Services to harvest or generate email addresses or otherwise determine the existence of unknown email addresses.
Last revised 01/14/2022.
